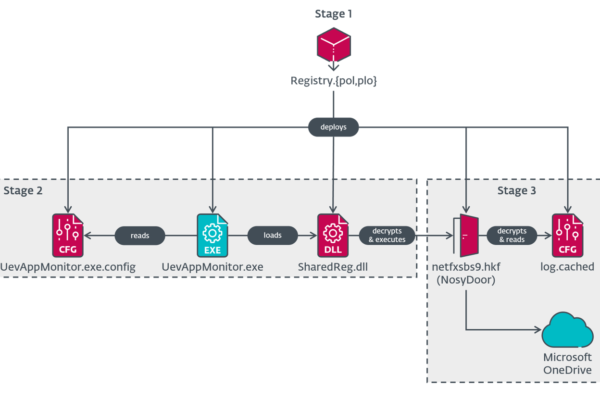
How enterprises can arm themselves
The good(ish) news, however, according to Beauceron’s Shipley, is that of the various types of phishes, from link-based, to attachment-based, to QR-code scanning, attachments tend to have a lower success rate. This is because they require additional cognitive effort and steps performed by the user, versus just clicking on a link in an e-mail.
Organizations should balance investment in email filters with security awareness training that’s done “frequently and effectively,” he noted. Ultimately, employees have to be motivated to remain vigilant.
CISOs must go beyond technical defenses and establish clear guardrails, advised SOCRadar’s Seker. This means blocking known-bad file types, deploying robust attachment sandboxing, and using endpoint detection to monitor suspicious file behavior post-delivery.