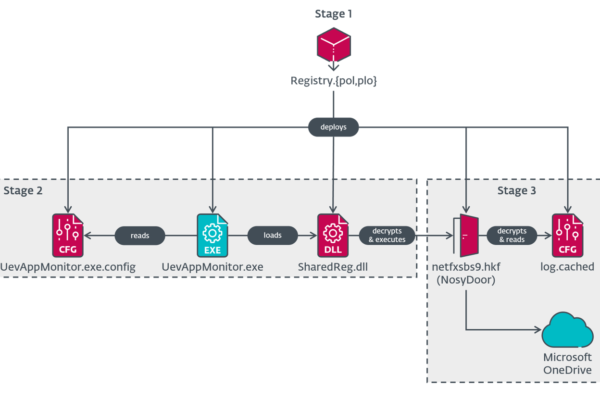
However, in the context of NDR, it is important to differentiate the capabilities of advanced platforms that provide features that modern cybersecurity stacks should include. For example, when evaluating different NDRs, it is important to ensure that they offer reliable forensics with long-term data retention. It is also crucial that they do not rely on NetFlow-based data. These are not supported in all environments and offer opportunities for sophisticated tunneling-based attacks.
Advanced NDR systems should even provide a retrospective view of network traffic to examine threat behavior before, during and after attacks. So if an indicator of compromise (IOC) is detected, security teams can examine the compromised hosts’ communications, detect lateral movement and determine if a data breach has occurred.
EDR, XDR, NDR: Together they are strong
To summarize, EDRs are designed to monitor and mitigate attacks on endpoints via connected computers and servers. However, only where agents can be deployed. Therefore, EDR does not work in some cloud-based hosting environments, for example. In contrast, XDRs provide a more unified platform approach to monitoring devices and data streams, but often lack the network context that NDRs provide through real-time packet monitoring.