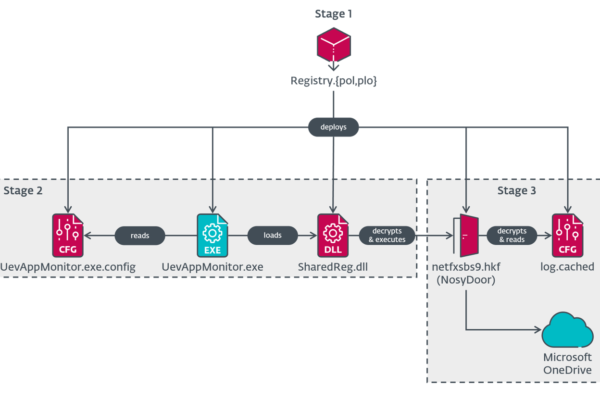
In addition to Cloudflare Turnstile challenges, the campaign uses subdomain rotation and geo-blocking for advanced evasion. Each victim gets a unique subdomain, sidestepping domain blacklists, while traffic from security vendors and cloud providers is blocked, so only real users reach the phishing page.
A call for layered and adaptive defenses
Countering Salty2FA might need something more than passwords and legacy controls, industry experts agreed. Darren Guccione, CEO of Keeper Security, argued that passkeys and passwordless authentication should be part of the strategy. “These technologies complement existing security measures by reducing reliance on traditional passwords, which remain a prime target for phishing,” he said.
Ontinue researchers have advised shifting away from static checks, which Salty2FA easily evades, toward sandboxing and run-time inspection of suspicious domains. They also stress that user awareness remains critical, as the phishing portals mimic legitimate sites so closely that technical controls alone cannot reliably stop them.