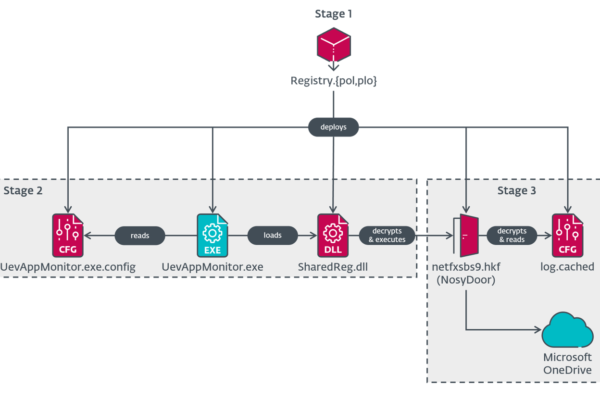
Researchers found that appending query strings like “?WSDL” or path parameters like “;.wadl” to protected endpoints ( like “/iam/governance/applicationmanagement/templates;.wadl”), would cause “SecurityFilter” in OIM’s web.xml to treat the route as “unauthenticated”—meaning that it requires no authentication.
Once past the filter, an attacker can reach the REST endpoint “/application/groovyscriptstatus” meant for syntax-checking Groovy code, not executing it. However, due to Groovy’s annotation processing, researchers demonstrated the ability to inject compile-time code that triggers outbound callbacks and code execution.
The flaw, tracked under CVE-2025-61757, received a critical severity rating of 9.8 out of 10, due to the ease of exploitability and presumably the existence of a zero-day abuse. “Given the complexity of some previous Oracle Access Manager vulnerabilities, this one is somewhat trivial and easily exploitable by threat actors,” researchers noted.