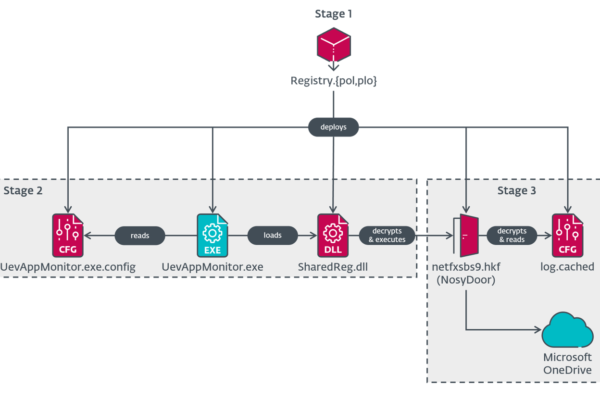
Fezbox claims to be a JavaScript/TypeScript utility library of “common helper functions,” organized into feature modules so users could pick and choose. Its README file, written in Chinese, includes the phrases “TypeScript types,” “high performance,” and “tests,” and describes a QR code module that could generate and analyze codes and auto-load necessary program components.
However, it didn’t mention that simply importing the library kicked off a backend process that retrieved and ran code hidden within a remote QR code image.
The code is minified (compressed) and hidden in larger blocks of seemingly benign “no-operation (no-op)” instructions that allow it to bypass security checks. A specific condition within the code checks whether the app is running in a development environment; if it is, “the code does nothing,” Brown explained, noting that this is a typical stealth tactic.