However, the ESET researchers suspect that this is a research project, a proof-of-concept (PoC) or an early version of a cybercrime tool that is still in the limited testing phase.
How the attack works
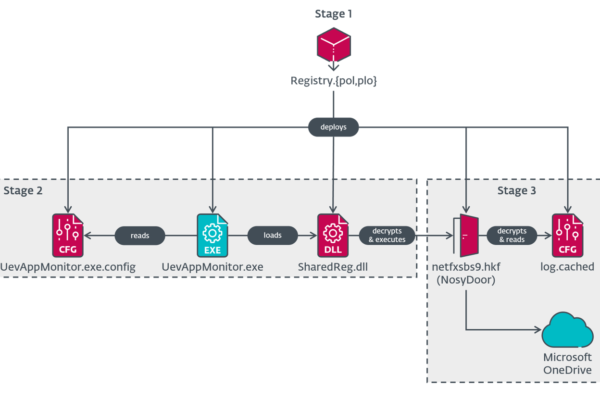
According to ESET, the ransomware exploits an already patched vulnerability (CVE-2024-7344) in a signed Microsoft EFI file (reloader.efi). An unsigned malicious file named cloak.dat is then loaded. In this way, integrity checks are bypassed and the malicious program can be executed even before the operating system starts.
The installer replaces the legitimate Windows bootloader with the vulnerable version. The malware then deliberately crashes the system, forcing a reboot. On boot, the compromised bootloader launches the HybridPetya bootkit and begins MFT encryption.