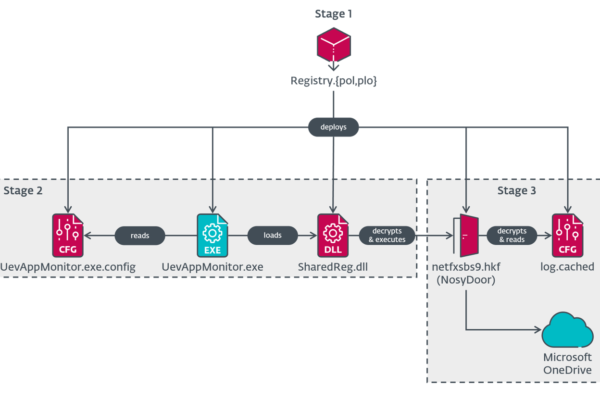
The recent SalesLoft Drift breaches revealed an uncomfortable truth that keeps me up at night, and should keep every CISO awake, too. Organizations weren’t breached through their vendor. They weren’t even breached through their vendor’s vendor. It appears they were compromised through their vendor’s acquired company, referred to as a “fourth-party,” via legacy OAuth tokens that had been dormant for 18 months.
As a point of fact, Drift historically integrated with both Salesforce (as a connected app) and Google Workspace (via its email integration). In this incident, attackers abused OAuth tokens associated with the Drift application to access Salesforce instances and accessed a limited number of Google Workspace accounts through the Drift email integration.
Public disclosures have not confirmed whether any abused tokens predated Salesloft’s 2024 acquisition of Drift. However, there is a real possibility that some tokens were legacy and inherited, which is an all‑too‑common scenario in M&A. Regardless of token provenance, the risk pattern is clear.